Bug bounty hunting is a career that is known for heavy use of security tools. These tools help the hunters find vulnerabilities in software, web applications and websites, and are an integral part of bounty hunting. Below is our top 10 list of security tools for bug bounty hunters.
- See what Beverly Briley (hackbar) has discovered on Pinterest, the world's biggest collection of ideas.
- Hackbarth Delivery Service specializes in Last Mile Delivery, Logistics, Warehousing and Transportation. 45 years of experience. Open 24/7/365.
- Dentist- Texas City, Tx Advanced Dentistry for Everyone Advanced Technology Convenient Location & Hours Affordable Quality Texas City's Trusted Dentist. As with most professions, dentistry requires a great deal of specialization.
Home › Forums › Add Hackbar in Mozilla Firefox 100% working This topic contains 1 reply, has 2 voices, and was last updated by IUsedToBeACave 1 week, 5 days ago. Author Posts August 24, 2020 at 4:01 am #298738 anonymousParticipant Add Hackbar in Mozilla Firefox 100% working August 24, 2020 at 4:01 am #298740 IUsedToBeACave. Info@hackbar.cc: Snail mail Bergheim Germany Number of members: 3 Members Location 50° 57' 10.29' N, 6° 38' 42.72' E Loading map. VCard download.
HackBar is a security auditing/penetration tool that is a Mozilla Firefox add-on. Bug bounty hunters will find that this tool allows them to test site security, XSS holes and SQL injections. Some of the advantages of HackBar include:
- All HackBar functions work on text that you currently have selected
- Hashing of MD5/SHA1/SHA256
- Sandbox-like textarea
- Useful MS SQL Server/MySQL shortcuts
If you are interested in HackBar, you can find it here.
Written in Python, Wfuzz is a tool that will help bug bounty hunters bruteforce web applications. Wfuzz is useful for sniffing out resources that are not linked such as directories and scripts, POST and GET parameter-checking for multiple kinds of injections, form parameter checking, fuzzing and other uses. Features that users will find attractive include:
- Default output is in HTML
- Capability to check multiple injection points
- Bruteforcing for all parameters
- Automatic/artificial request time delays
- Results can be hidden via word numbers, return code, line numbers and regex
When checking for vulnerabilities in your websites, IronWASP is going to quickly become one of your best friends. This web security scanner is open source and free to use, and more powerful than you think it would be for being so wallet-friendly. Some great features include:
- Login sequence recording is supported
- False-positive and negative-positive detection are supported
- Reporting is available in both RTF and HTML formats
- Easy to use and with a simple-to-understand GUI, even an inexperienced information security employee can quickly use it
If IronWASP has piqued your interest, you can find it here. Tuff torq owners manual.
Not to be left out, mobile applications are definitely a contemporary area of interest for bug bounty hunters. One of the best among them is INalyzer for the iOS platform. Hosted by App Sec Labs, INalyzer makes manipulation of iOS applications a breeze. Tampering with methods and parameters is available and INalyzer can target closed applications, which means that your black-box project can now be considered gray-box. For more information on INalyzer, click here.
Wapiti is a command-line application tool that allows bug bounty hunters to audit the security of websites and web applications. Operationally, Wapiti crawls web applications with black-box scans and looks for points where it can inject code. Autodata crack dongle key emulator. When Wapiti finds a list of forms, form inputs and URLs, it acts like a fuzzer by injecting payloads to check for script vulnerability. Some notable features include:
Hackbarthdelivery.com
- Server-side request forgery
- Reflected and permanent XSS injection
- ShellShock
- Includes a buster module that allows for bruteforcing filenames and directories on a target web server
- POST HTTP and GET attack methods are supported
- The scan process includes an option to set maximum scan time
Sometimes as a security researcher, especially for bug bounty hunters, all you have is an IP address to work with. This may seem trivial to the untrained eye, but experienced hunters know you can really do a lot with it. Hosted on DomainTools, Reverse IP Lookup will find all domains hosted on the IP, track domains that are coming and going, and output result data into .csv reports. IP lookups are free if you are a DomainTools Personal or Enterprise member. To give Reverse IP Lookup a go, click here.
Hosted on GitHub, DNS-Discovery is a great tool for the bug bounty hunter. This tool is a multithreaded (a breath of fresh air from some other similar tools) subdomain bruteforcer that uses a word list to concatenate with a domain to look for subdomains. DNS-Discovery allows for resolution and display of both IPv4 and IPv6.
Ethical Hacking Training – Resources (InfoSec)
Google Dorks is a solid go-to to use when searching for hidden data and access pages on websites. This tool relies in part on the part of the website indexing power of Google and this volume of data is useful for bug bounty hunters. Google Dorks also does a good job with network mapping and can assist in finding subdomains.
While not a 'tool' in the purest sense, Vulnerability Lab is definitely a helpful website that hunters would do well to keep in the toolbox. Vulnerability Lab is a project that provides vulnerability research, vulnerability assessments and bug bounties. Among some of the most useful aspects are the web application vulnerabilities and website vulnerabilities. This would definitely be one of the first resources I would consult when beginning a bug bounty hunt.
The top spot on the list of security tools for bug bounty hunters belongs to Burp Suite, and for good reason. Burp Suite is an integrated security-testing platform for web applications that gives hunters what they need to get the job done. It allows you to perform scans on everything you want from full crawls to individual URLs and covers over 100 generic vulnerabilities. Burp Suite also supports many kinds of attach insertion points and nested insertion points. At the end of the day, Burp Suite offers a clear and comprehensive presentation of vulnerabilities. This is a paid tool and can be found
here.
Firefox, No doubt one of the best and popular internet browser . but many of us don't know a lot of thing which can make it perfect browser for computer geeks. So now i'm going to tell you some important firefox addons we must have.
1. FOX TAB
3D in your browser! FoxTab brings innovative 3D functionality to your Firefox. Now you can access your most favorite sites from the familiar FoxTab interface. FoxTab is a popular 3D tab management extension.
FoxTab powers Firefox with the following main features:
- Top Sites (aka Speed Dial) for quickly accessing your favorite web sites.
- Tab Flipper – to easily flip between opened tabs using mouse or keyboard gestures.
- Recently Closed Tabs – for reopening a tab that was recently closed.
- Choose between 6 attractive 3D layouts.
Download Link:
2. GREASE MONKEY
Grease monkey extension allows you to customize the way a webpage displays using small bits of JavaScript. …!!
Download Link:
https://addons.mozilla.org/en-US/firefox/addon/748/
3. TAMPER DATA:
Use tamperdata to view and modify HTTP/HTTPS headers and post parameters. Trace and time http response/requests. Security test web applications by modifying POST parameters.
FYI current version of Google Web Accelerator is incompatible with the tampering function of TamperData. Your browser will crash.
Download Link:
https://addons.mozilla.org/en-US/firefox/addon/966/
4. XSS ME
Cross-Site Scripting (XSS) is a common flaw found in todays web applications. XSS flaws can cause serious damage to a web application. Detecting XSS vulnerabilities early in the development process will help protect a web application from unnecessary flaws. XSS-Me is the Exploit-Me tool used to test for reflected XSS vulnerabilities
Download Link:
5. Sparky
Sparky is Alexa Internet's free Firefox status bar plugin. Sparky accompanies you as you surf, providing you with Alexa data about the sites you visit without interrupting your browsing.
- Discover website traffic trends — Is this site getting more popular, or less?
- Get detailed traffic information including Reach and Rank — How does this site's traffic compare to other sites on the Web?
- Surf more efficiently with Related Links for each page — If I like this site, are there others that I might want to visit?
- Gracefully navigate past dead end error pages — Enable Sparky's optional custom error handling to get relevant alternative links when your browser encounters a network error.
Plus, as you browse with Sparky, you're helping to make the Web a better place for everybody by contributing to the traffic information that Alexa provides.
Download Link:
6. SQL INJECT ME
SQL Injection vulnerabilites can cause a lot of damage to a web application. A malicious user can possibly view records, delete records, drop tables or gain access to your server. SQL Inject-Me is Firefox Extension used to test for SQL Injection vulnerabilities.
SQL Inject Me is the Exploit-Me tool used to test for SQL Injection vulnerabilities.
The tool works by submitting your HTML forms and substituting the form value with strings that are representative of an SQL Injection attack.
The tool works by sending database escape strings through the form fields. It then looks for database error messages that are output into the rendered HTML of the page.
The tool does not attempting to compromise the security of the given system. It looks for possible entry points for an attack against the system. There is no port scanning, packet sniffing, password hacking or firewall attacks done by the tool.
Cyberlink bd advisor. Download Link:
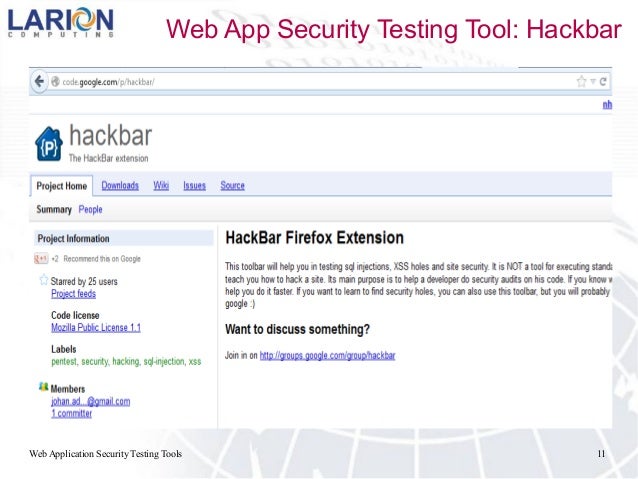
7. HACKBAR
This toolbar will help you in testing sql injections, XSS holes and site security. It is NOT a tool for executing standard exploits and it will NOT teach you how to hack a site. Its main purpose is to help a developer do security audits on his code. If you know what your doing, this toolbar will help you do it faster. If you want to learn to find security holes, you can also use this toolbar, but you will probably also need a book, a lot of Google and a brain
Hackbar License

Home › Forums › Add Hackbar in Mozilla Firefox 100% working This topic contains 1 reply, has 2 voices, and was last updated by IUsedToBeACave 1 week, 5 days ago. Author Posts August 24, 2020 at 4:01 am #298738 anonymousParticipant Add Hackbar in Mozilla Firefox 100% working August 24, 2020 at 4:01 am #298740 IUsedToBeACave. Info@hackbar.cc: Snail mail Bergheim Germany Number of members: 3 Members Location 50° 57' 10.29' N, 6° 38' 42.72' E Loading map. VCard download.
HackBar is a security auditing/penetration tool that is a Mozilla Firefox add-on. Bug bounty hunters will find that this tool allows them to test site security, XSS holes and SQL injections. Some of the advantages of HackBar include:
- All HackBar functions work on text that you currently have selected
- Hashing of MD5/SHA1/SHA256
- Sandbox-like textarea
- Useful MS SQL Server/MySQL shortcuts
If you are interested in HackBar, you can find it here.
Written in Python, Wfuzz is a tool that will help bug bounty hunters bruteforce web applications. Wfuzz is useful for sniffing out resources that are not linked such as directories and scripts, POST and GET parameter-checking for multiple kinds of injections, form parameter checking, fuzzing and other uses. Features that users will find attractive include:
- Default output is in HTML
- Capability to check multiple injection points
- Bruteforcing for all parameters
- Automatic/artificial request time delays
- Results can be hidden via word numbers, return code, line numbers and regex
When checking for vulnerabilities in your websites, IronWASP is going to quickly become one of your best friends. This web security scanner is open source and free to use, and more powerful than you think it would be for being so wallet-friendly. Some great features include:
- Login sequence recording is supported
- False-positive and negative-positive detection are supported
- Reporting is available in both RTF and HTML formats
- Easy to use and with a simple-to-understand GUI, even an inexperienced information security employee can quickly use it
If IronWASP has piqued your interest, you can find it here. Tuff torq owners manual.
Not to be left out, mobile applications are definitely a contemporary area of interest for bug bounty hunters. One of the best among them is INalyzer for the iOS platform. Hosted by App Sec Labs, INalyzer makes manipulation of iOS applications a breeze. Tampering with methods and parameters is available and INalyzer can target closed applications, which means that your black-box project can now be considered gray-box. For more information on INalyzer, click here.
Wapiti is a command-line application tool that allows bug bounty hunters to audit the security of websites and web applications. Operationally, Wapiti crawls web applications with black-box scans and looks for points where it can inject code. Autodata crack dongle key emulator. When Wapiti finds a list of forms, form inputs and URLs, it acts like a fuzzer by injecting payloads to check for script vulnerability. Some notable features include:
Hackbarthdelivery.com
- Server-side request forgery
- Reflected and permanent XSS injection
- ShellShock
- Includes a buster module that allows for bruteforcing filenames and directories on a target web server
- POST HTTP and GET attack methods are supported
- The scan process includes an option to set maximum scan time
Sometimes as a security researcher, especially for bug bounty hunters, all you have is an IP address to work with. This may seem trivial to the untrained eye, but experienced hunters know you can really do a lot with it. Hosted on DomainTools, Reverse IP Lookup will find all domains hosted on the IP, track domains that are coming and going, and output result data into .csv reports. IP lookups are free if you are a DomainTools Personal or Enterprise member. To give Reverse IP Lookup a go, click here.
Hosted on GitHub, DNS-Discovery is a great tool for the bug bounty hunter. This tool is a multithreaded (a breath of fresh air from some other similar tools) subdomain bruteforcer that uses a word list to concatenate with a domain to look for subdomains. DNS-Discovery allows for resolution and display of both IPv4 and IPv6.
Ethical Hacking Training – Resources (InfoSec)
Google Dorks is a solid go-to to use when searching for hidden data and access pages on websites. This tool relies in part on the part of the website indexing power of Google and this volume of data is useful for bug bounty hunters. Google Dorks also does a good job with network mapping and can assist in finding subdomains.
While not a 'tool' in the purest sense, Vulnerability Lab is definitely a helpful website that hunters would do well to keep in the toolbox. Vulnerability Lab is a project that provides vulnerability research, vulnerability assessments and bug bounties. Among some of the most useful aspects are the web application vulnerabilities and website vulnerabilities. This would definitely be one of the first resources I would consult when beginning a bug bounty hunt.
The top spot on the list of security tools for bug bounty hunters belongs to Burp Suite, and for good reason. Burp Suite is an integrated security-testing platform for web applications that gives hunters what they need to get the job done. It allows you to perform scans on everything you want from full crawls to individual URLs and covers over 100 generic vulnerabilities. Burp Suite also supports many kinds of attach insertion points and nested insertion points. At the end of the day, Burp Suite offers a clear and comprehensive presentation of vulnerabilities. This is a paid tool and can be found
here.
Firefox, No doubt one of the best and popular internet browser . but many of us don't know a lot of thing which can make it perfect browser for computer geeks. So now i'm going to tell you some important firefox addons we must have.
1. FOX TAB
3D in your browser! FoxTab brings innovative 3D functionality to your Firefox. Now you can access your most favorite sites from the familiar FoxTab interface. FoxTab is a popular 3D tab management extension.
FoxTab powers Firefox with the following main features:
- Top Sites (aka Speed Dial) for quickly accessing your favorite web sites.
- Tab Flipper – to easily flip between opened tabs using mouse or keyboard gestures.
- Recently Closed Tabs – for reopening a tab that was recently closed.
- Choose between 6 attractive 3D layouts.
Download Link:
2. GREASE MONKEY
Grease monkey extension allows you to customize the way a webpage displays using small bits of JavaScript. …!!
Download Link:
https://addons.mozilla.org/en-US/firefox/addon/748/
3. TAMPER DATA:
Use tamperdata to view and modify HTTP/HTTPS headers and post parameters. Trace and time http response/requests. Security test web applications by modifying POST parameters.
FYI current version of Google Web Accelerator is incompatible with the tampering function of TamperData. Your browser will crash.
Download Link:
https://addons.mozilla.org/en-US/firefox/addon/966/
4. XSS ME
Cross-Site Scripting (XSS) is a common flaw found in todays web applications. XSS flaws can cause serious damage to a web application. Detecting XSS vulnerabilities early in the development process will help protect a web application from unnecessary flaws. XSS-Me is the Exploit-Me tool used to test for reflected XSS vulnerabilities
Download Link:
5. Sparky
Sparky is Alexa Internet's free Firefox status bar plugin. Sparky accompanies you as you surf, providing you with Alexa data about the sites you visit without interrupting your browsing.
- Discover website traffic trends — Is this site getting more popular, or less?
- Get detailed traffic information including Reach and Rank — How does this site's traffic compare to other sites on the Web?
- Surf more efficiently with Related Links for each page — If I like this site, are there others that I might want to visit?
- Gracefully navigate past dead end error pages — Enable Sparky's optional custom error handling to get relevant alternative links when your browser encounters a network error.
Plus, as you browse with Sparky, you're helping to make the Web a better place for everybody by contributing to the traffic information that Alexa provides.
Download Link:
6. SQL INJECT ME
SQL Injection vulnerabilites can cause a lot of damage to a web application. A malicious user can possibly view records, delete records, drop tables or gain access to your server. SQL Inject-Me is Firefox Extension used to test for SQL Injection vulnerabilities.
SQL Inject Me is the Exploit-Me tool used to test for SQL Injection vulnerabilities.
The tool works by submitting your HTML forms and substituting the form value with strings that are representative of an SQL Injection attack.
The tool works by sending database escape strings through the form fields. It then looks for database error messages that are output into the rendered HTML of the page.
The tool does not attempting to compromise the security of the given system. It looks for possible entry points for an attack against the system. There is no port scanning, packet sniffing, password hacking or firewall attacks done by the tool.
Cyberlink bd advisor. Download Link:
7. HACKBAR
This toolbar will help you in testing sql injections, XSS holes and site security. It is NOT a tool for executing standard exploits and it will NOT teach you how to hack a site. Its main purpose is to help a developer do security audits on his code. If you know what your doing, this toolbar will help you do it faster. If you want to learn to find security holes, you can also use this toolbar, but you will probably also need a book, a lot of Google and a brain
Hackbar License
# The advantages are:
– Even the most complicated urls will be readable
– The focus will stay on the textarea, so after executing the url (Ctrl+Enter) you can just go on typing / testing
– The url in textarea is not affected by redirects.
– I tend to use it as a notepad
– Useful tools like on the fly uu/url decoding etc.
– All functions work on the currently selected text.
– MD5/SHA1/SHA256 hashing
– MySQL/MS SQL Server/Oracle shortcuts
– XSS useful functions
– And lots more Go test it!
# Shortcuts
– Load url ( Alt + A )
– Split url ( Alt + S )
– Execute ( Alt + X, Ctrl + Enter )
– INT -1 ( Alt – )
– INT +1 ( Alt + )
– HEX -1 ( Ctrl Alt – )
– HEX +1 ( Ctrl + Alt + )
– MD5 Hash ( Alt + M )
– MySQL CHAR() ( Alt + Y )
– MS SQL Server CHAR() ( Alt + Q )
Download Link:
